Cybersecurity threats, like computer worms, are evolving quickly, making it crucial to understand how they work and take preventive steps. Keeping up in knowledge or defenses leaves you vulnerable to attacks that can disrupt your system and expose sensitive data.
Unlike traditional viruses, computer worms spread independently, rapidly infecting networks and causing significant harm without user interaction.
What is a Computer Worm, and How Does it Work?

A computer worm is a malware that self-replicates and spreads independently across networks by exploiting operating systems or software vulnerabilities. Unlike viruses, worms do not require an existing program or file to attach themselves to. Instead, they use weaknesses in your network or system to infiltrate and proliferate.
Once a worm has entered your system, it can cause various problems, including slowing down your network, deleting critical files, or creating backdoors for cybercriminals to access your data. Worms’ ability to spread without human intervention makes them especially dangerous, as they can quickly infect many devices.
How to Remove a Computer Worm
If a computer worm has infected your system, immediate action is necessary to prevent further damage. Below are steps to remove the malware and secure your system.
Isolate the Device
Isolating your device from the network is a crucial first step when dealing with a computer worm. Disconnecting from the internet or any shared network helps prevent the malware from spreading to other connected devices. This action minimizes the worm’s ability to replicate across multiple systems.
Remove the Malware
Use a trusted antivirus or anti-malware program to remove a worm from your computer. Most security software is equipped to identify and eliminate worms. Make sure to run a comprehensive system scan, as worms may hide in various parts of your system. After detecting the malware, follow the program’s instructions to remove it entirely.
Use a third-party PC cleaner like Tweaking to combat computer worms. Tweaking automatically detects and resolves infection-related policies, repairs most Windows files after malware attacks, fixes Windows update issues, restores broken registry keys, and manages critical OS files with advanced backup and firewall features.
Download and install Tweaking now.
How to Prevent Computer Worm Infections
Preventing a computer worm from infecting your system is far better than dealing with the aftermath. Follow these best practices to safeguard your Windows PC from potential threats.
Practice Safe Internet Usage
Safe browsing habits are crucial for avoiding malware infections. Avoid downloading files or software from untrusted sources, and always verify the legitimacy of the websites you visit. Regularly clearing your browser cache and history also helps reduce the risk of exposure to harmful content.
Be Cautious with Email Attachments and Links
Many worms spread through email attachments or malicious links. Always verify the sender before opening attachments, and be cautious with unexpected emails. If an email seems suspicious or too good to be true, it’s best to delete it rather than risk opening a harmful attachment.
Avoid Clicking on Pop-up Ads
Pop-up ads, especially those that offer free software or services, can often be sources of malware, including worms. Refrain from clicking on any pop-up ads, which may redirect you to compromised sites. An ad blocker can further reduce the chances of such malicious ads.
Use a VPN for Additional Security
A Virtual Private Network (VPN) encrypts your data and adds an extra layer of security to your internet connection. This helps prevent worms from exploiting vulnerabilities in your network, especially when you’re using public Wi-Fi. Opt for a reputable VPN to ensure your privacy and security online.
Keep Your Software Updated
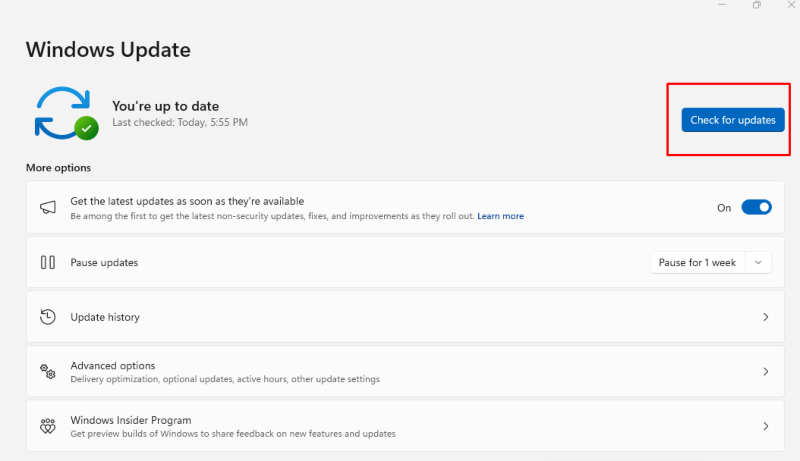
Keeping your operating system, antivirus, and other software up to date is one of the most effective ways to protect your PC from worms. Cybercriminals often exploit outdated software to infect systems. Enabling automatic updates can protect your system with the latest security patches and features.
Regularly Update Your Passwords
Weak or outdated passwords can allow worms to infiltrate your system quickly. It’s important to regularly update your passwords and ensure they are strong by including a mix of uppercase and lowercase letters, numbers, and special characters. Using unique passwords for each account further reduces the risk of unauthorized access.
Use Automatic Updates and Malware Removal Tools
Incorporating third-party tools like Tweaking can enhance. Tweaking is particularly effective in identifying and removing worms before they can cause significant damage.
Educate Yourself on Cybersecurity

One of the best defenses against computer worms is awareness. By staying informed about the latest cybersecurity threats and learning best practices for online safety, you can protect your device and others connected to your network. Sharing this knowledge with colleagues, friends, and family can help them stay secure.
Signs That Your Computer May Have a Worm
Recognizing the early signs of a worm infection can help you act quickly before the situation worsens. Here are common symptoms of a computer worm:
- Sluggish system performance: Worms consume system resources, leading to slower performance.
- Unusual network activity: A worm spreading to other devices may result in a sudden spike in network traffic or data usage.
- Unauthorized file changes: New files or programs may appear without your consent.
- Increased pop-up ads: A sudden increase in pop-ups, even outside of web browsing, could indicate malware.
- Disabled security software: Worms may attempt to turn off your antivirus or firewall to avoid detection.
- Low disk space: Excessive worm replication can take up storage space, leaving little room on your hard drive.
- System crashes: Frequent system crashes or unresponsive programs may also indicate a worm infection.
Menzi Sumile
Verified at:
29/05/2024 06:37
Leave a Reply